
Nearly three-quarters of all government-related privacy breaches are caused by simple human error — not a result of hackers trying to steal our personal information.
 That’s the key finding in a report issued yesterday (on International Data Privacy Day) by B.C. Information and Privacy Commissioner Elizabeth Denham, who last year launched the province’s first examination of privacy breach management practices.
That’s the key finding in a report issued yesterday (on International Data Privacy Day) by B.C. Information and Privacy Commissioner Elizabeth Denham, who last year launched the province’s first examination of privacy breach management practices.
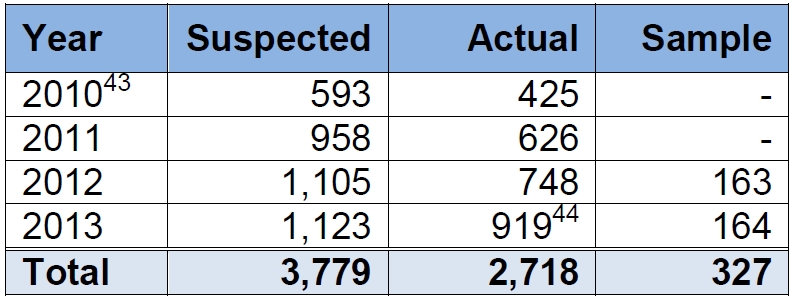
From 2010 through 2013, British Columbia’s chief information officer received 2,718 reports of government-related privacy breaches. Of those, nearly 72 per cent were caused by administrative error — typically, mail or e-mail being sent to the wrong address.
“The overwhelming majority of them involve human error,” says Ryan Berger, who chairs the privacy committee at Bull Housser & Tupper LLP in Vancouver. “When 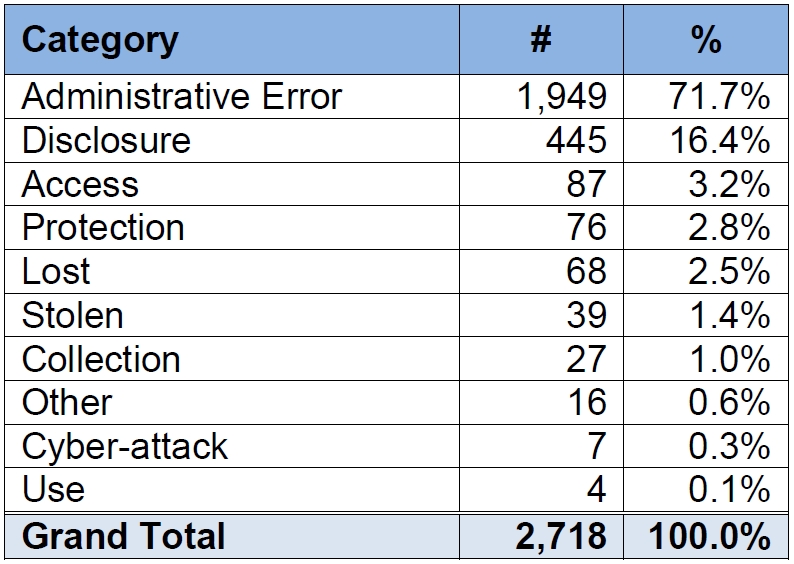 we read stories in the newspapers, it’s often the systemic or hacker-related breaches, but the rubber meets the road when it comes to management and education of people. That’s where the breaches are.”
we read stories in the newspapers, it’s often the systemic or hacker-related breaches, but the rubber meets the road when it comes to management and education of people. That’s where the breaches are.”
In general, Denham was satisfied with the foundation that has been laid for breach-management systems. She notes the CIO’s office has done a good job of collecting information about privacy breaches quickly and notifying those affected within a reasonable time frame.
However, the report urges the CIO to adopt a more proactive position by analyzing the information about breaches, devising best practices, and ensuring — through the establishment of a compliance officer and regular audits — that the ministries comply.
“Most privacy breaches are preventable, but only if organizations take the opportunity to learn from their mistakes and implement lasting preventative strategies,” said Denham in a released statement.
Indeed, the report underscores the importance of analysis and risk evaluation to ensure the CIO understands how breaches are happening and to focus their efforts on methods that deal specifically with those gaps. For instance, where administrative error is the culprit, increased training may be the solution.
“I think that makes a lot of sense,” says Berger. “You have to take a risk-based approach and allocate your resources to the areas that result in the most number of breaches and the most significant breaches. The government knows where those are; they have to pay attention to their own figures.”
Denham’s report also recommends the province establish specific criteria for when a suspected privacy breach is reported — both to the CIO’s office and, for more serious breaches, to the commissioner’s office.
“I think the reporting to her office has been sometimes yes, sometimes no, and decided on a one-off basis,” says Tamara Hunter, who leads the privacy law compliance group at Vancouver-based Davis LLP. “I think she’s saying, ‘No, you should have set criteria that gets applied in every single instance. You need specific criteria for when you report and when you don’t.’”
Hunter adds, while the report deals specifically with government-related privacy breaches, businesses should also take note: “I’m sure that, if there are these areas that can be improved in the public sector, they’re probably at least as applicable, if not more applicable, in the private sector. I would just urge private businesses to read through this.”